
By John F. Muffler
U.S. Marshal (Ret.)
In my December 2014 Judicial Edge article announcing the release of the Judicial Security Survey (JSS), I talked about using the survey as a vehicle to develop short and long-term forecasts and dedicating resources in an effort to secure the judicial process, specifically its independence. What makes democracy work is the impartiality exercised by its judicial officers. Sound protective measures are the fulcrum point upon which judicial independence balances.
“I was almost murdered by a litigant. He killed his ex-wife’s husband, tried to kill her but she managed to escape. He then shot himself when he couldn’t find her. He had a list in his possession with my name, home address, where I was presiding that day, guns, ammo, and the makings of Molotov cocktails. Had his ex-wife not escaped, he clearly was coming after me next. In furtherance of his master plan he rented a car and disguised himself with a wig. I had last had any contact with him 12 years earlier when I presided over their divorce.”
— Testimonial of National Judicial College participant Judge “X”1 taken from the 2014 Judicial Security Survey
Related Stories
» The NJC Releases Report from 2014 Judicial Security Survey
» Protecting Your Castle: Residential Security for Judges
Threats and attacks to judicial officers are not just a phenomenon in the United States; they are borderless, global occurrences2 that do not discriminate regarding type of case or jurisdiction level where litigated. Much attention is given to attacks against Title III judges and that may be because there is good, tangible data available. Because attacks to them are rare, when they do occur, they tend to happen at home and make the national news cycle. The JSS clearly reflects threats and security considerations beyond Title III judges are present and occurring at an alarming rate, which supports hundreds of conversations I’ve had with judges about their fears.
Criticality of Threat Assessment Programs
Therein lies a key problem; much of these threats, inappropriate communications, and contacts (TICCs) are not documented by a judicial security/law enforcement element. For those that are reported, questions should be asked by judges: how are they being triaged? By whom? Are even benign communications taken seriously? Who is responsible for the identification, assessment, mitigation, management, and investigation of the reported incident? Judges need to fully understand the answers to these questions, as they are paramount to their survival.
Bailiffs and court security may not have legal authority to investigate. Law enforcement and investigators in your town may not work for the same chain-of-command, resulting in weak links in the communication. Because this is a judicial branch threat investigation, it may fall to the Office of the Sheriff, the police department, or district attorney’s investigators. Specific training and experience in threat assessment, a non-traditional law enforcement responsibility, is necessary. What threat assessment tools and tactics do they use? Shared responsibilities are not uncommon. This happens at the federal level between the Federal Bureau of Investigation, who would be conducting the criminal investigation, and the U.S. Marshals, responsible for conducting the protective investigation and maintaining protective responsibility.
Once having reported the threat issue, it is easy for judges to have a false sense of security and to assume the matter has concluded. However, it is at this juncture that two-way communication and regular updates commence between judges and the investigative team. Although these collaborative efforts are crucial throughout the duration of the threat investigation, judges need not be, nor should they be, part of the investigative team.
It is equally important for security or law enforcement to share threat information, even a non-specific target threat. This must be conveyed to judicial officers. The process of how generalized threats are conveyed to all judicial officers should be a well-thought-out protocol amongst justice system entities. If reported, a threat can heighten a judge’s own security intuition. Only then can each individual judge determine what that general threat may mean to him/her. For example, schools today broadcast non-specific threats to parents and students via automated phone calls, emails and social media, enabling all to make an informed decision and, perhaps more importantly, raise the security awareness red flag.
Case in point, on Nov. 6, 2015, Travis County Texas District Judge July Kocurek was ambushed in her home driveway, shot point-blank, putting her attack-and the attack to an institution-in the national spotlight. Thankfully, she and her children, also in the car, survived. It was a Friday evening and she was returning home from a high school football game. Normally, when driving up to her house, she would hit the security gate remote in her car, roll past, and secure the gate behind her, practicing good home security measures (and this security gate was a well-thought-out security measure).
But this time was different. A bag of trash blocked the vehicle’s ability to roll through and she came to a stop3. This simple tactic by the shooter made her a stationary target. Her son exited the car to remove the bag and suddenly gun blasts rang out striking her but not killing her. In the ensuing investigation, it was determined that a “non-credible threat” to “kill a judge” was received by investigators two weeks before4. However, this information was not shared with local judiciary. It should be noted that a person of interest, who had a pending case before Judge Kocurek, was arrested two weeks later for the attempted assassination.
Loading one’s security intuition, can only be done when getting as much information as possible, credible or not. A law enforcement officer’s development of reasonable suspicion and probable cause is much the same. Development of intuition and suspicion are based on life experiences and practices when the collective information is gathered and mentally processed in a reasonably objective way. What is out of place? Can I/should I act? Does a bag at a gate belong there on a non-trash pickup night? Am I aware of a threat to kill a judge? Without data, one is not fully informed to have heightened awareness and take necessary precautions.
While it is important and relevant to look at the statistics compiled by agencies specifically mandated to protect judges and the judicial process, such as data maintained by the United States Marshals Service, it is equally important to understand what threat management tools are in the toolbox of like-agencies, private and government, that mitigate risk to celebrities, government officials, business owners, and private individuals.
What’s in Your Prescription?
In medicine, a doctor can only make an accurate diagnosis and administer the best care when the patient gives as much information about the problem. This is analogous to descriptive, predictive, and prescriptive data analytics and directly applicable to assessing threats. As Dr. Michael Wu, Lithium Technologies, told InformationWeek’s Jeff Bertolucci, “the purpose of descriptive analytics is to summarize what happened…predictive is the next step in data reduction using varying methods to study recent and historical data, thereby allowing analysts to make predictions about the future. Predictive analytics can only forecast what might happen in the future because all predictive analytics are probabilistic in nature.” It is not a genie in a bottle but a recommended course of action. The assessment, i.e. the medicine to be prescribed, is based on received information and may help prevent a tragic outcome.
Here is a simple example of an intuitive assessment as explained to me in a recent interview with Gavin de Becker, author of numerous books on threat assessment and security and creator of MOSAIC, a quantifiable, proven threat assessment process. For the sake of argument, let’s say a judge rules against a particular litigant and that during and after the legal process the judge was receiving unusual or inappropriate communications. Now let’s say it was known that the litigant owned a firearm. Does this make a difference in assessing potential risk? Maybe, maybe not, depending on other factors but it would be important to know. Now how about if it is discovered that the litigant only purchased that firearm after he lost the case? Does this make a difference in assessing potential risk? Intuitively, the answer will be found on the hairs standing on the back of your neck.
MOSAIC systems ask a series of questions and then compares the current constellation of factors to expert opinion and to past cases in which the outcome is known. The system can then report whether the current situation is most similar to cases that escalated, or most similar to cases that did not escalate. Like computer-aided engineering cannot design a jet, but can help the designer, MOSAIC does not make predictions, but can help the assessor.5
The only way an individual can make these assessments is to collect pieces of the puzzle, the medley of different experiences and information, to inform and prescribe best possible outcomes. Courts, often under scrutiny for their decision-making by affected parties or simply because they represent government, need threat management programs to help stabilize the institution. Educational programs on security are equally as important too. These two pillars of judicial security will enhance security measures and counter-measures and strengthen mindset.
Behaviors of the Injustice Collectors
Attacks to judicial officers are not unlike attacks to other members of society. These attacks can be divided into two categories: targeted or planned and affected or reactive violence6. Physiologically, reactive violence can be described as intense autonomic arousal, such as an emotional outburst. Family law cases, unexpected judicial decisions, or cases where family members cross paths in the close quarters of the courtroom are events wherein affected violence transpires. Conversely, there is little or no autonomic arousal in a planned attack. These types of attacks are synonymous to murders of all judges killed as a result of their position and Hollywood celebrities, like actress Rebecca Schaeffer, who was stalked then murdered. Assuredly, Judge X was being targeted for assassination by a former litigant.
Actors of planned violence find themselves along a “Pathway to Violence” as described in Calhoun and Weston’s research, Contemporary Threat Management. Along this continuum, attackers progress along identifiable steps of grievance, ideation, research and attack planning, pre-attack preparation, probing and breaching, and finally the attack. Gene Deisinger, Ph.D., Managing Partner, SIGMA Threat Management Associates, PA, describes the pathway succinctly, “at its foundation it begins with a perceived or real wrongdoing. Often times these people who come to our attention are referred to as injustice collectors. It may not be one grievance, but a series of grievances over time. To that they attribute the ideation of the use of violence to address the grievance.” This can take time (days, weeks, months, or even years) for some people to develop in the actor’s mind. Meanwhile, they move from ideation to planning, investing more emotions into the process.
According to Dr. Deisigner, “many stop at the planning phase due to too many barriers or the issue resolves itself somehow. The next phase is the acquisition where they acquire the means, methods, the opportunity and the proximity to their target and that is when concern increases significantly.” Probing, breaching, and surveillance follows, which feeds back into the ideation, planning, and acquisition phases. The further the actor is along the continuum, the greater chances of the attack transpiring. This is where Courts need proper threat management tools. As Dr. Deisinger states, “it is incumbent upon processes that are identifying, detecting and assessing to be prepared to respond the further they see someone along the continuum.” We also see this type of behavior in active shooters across the country today.
Judge X describes this exact pathway when he answered the question, “If you have been threatened, by what means was the threat conveyed?” His potential attacker’s grievance and ideation escalated over a period of time, “I had last had contact with him 12 years earlier…” The Judge describes the intensity of effort and the acquisition phase rather clearly, “in his possession…guns, ammo, Molotov cocktails…In furtherance of his master plan he had rented a car a disguised himself with a wig.” In the probing, breaching and surveillance phase we see, “he had a list in his possession with my name, home address, courthouse where I was presiding that day…” Alarmingly, Judge X was one of 593 judges (51.88 percent) in the survey to answer yes to that question.
Effect on Independence
In the survey, 21 judges reported being physically attacked because of their position. When asked “if concern for your security ever caused you to hesitate before taking certain action in a case”, 945 (82.89 percent) said it did not but 195 (17.11 percent) said it did. In another question, 217 (19 percent) said concerns for their security did cause them to change their professional conduct. Three hundred and fifty-five (31.11%) said their family feels unsafe because of their position as a judge and over 80% responded that they worry about their own safety due to their positon. The Honorable Chuck Weller, Washoe County Nevada District Court, corroborates these type of stressors and effects in his “Statutory Response to Court Security Concerns” dissertation stating, “disturbingly, judges feared that becoming a victim of violence might cast a shadow over their perceived capacity as a jurist, reducing their willingness to report incidents that might identify dangerous persons.” These staggering numbers underscore the importance of security, threat management, and educational programs.
Conclusion
The judicial process can ill afford to not have foundational security measures and counter-measures in place beyond badges and guns, magnetometers and hand-wands, cameras, duress alarms and bollards. Those are important components to the physical security of the courthouse making planned violence away from that hard-target environment easier and why the home has proven to be the likely attack point. Judges are members of the community, live in the open, and have to understand there is an inherent risk to their position. The black robe is on them 24/7/365, not just at the courthouse.
Those responsible for securing the court, and the guardians of our liberty, need to evaluate budgets and resources to have and be in compliance with threat management protocols. As Dr. Deisinger points out, having processes in place to mitigate and intervene is critical; it is the fulcrum point by which democracy and judicial independence pivots.
- The survey anonymously measured threats to hearing officers, administrative, appellate, tribal, military, state and local judges.
- http://shanghaiist.com/2016/03/01/beijing_judge_gunned_down.php
- http://www.statesman.com/news/news/local/investigator-kocurek-shooting-was-murder-attempt/npJcS/
- http://kxan.com/2015/12/14/two-weeks-before-kocurek-shooting-authorities-were-warned-of-threat/
- https://www.mosaicmethod.com/
- Virginia Center for Policing Innovation. U.S. Department of Justice, Bureau of Justice Assistance (2012). Violence interdiction: A proactive approach to mitigating conflict. Richmond, VA: Virginia Center for Policing Innovation

This month’s one-question survey* of NJC alumni asked, “How is 2024 shaping up for you and your court?�...

RENO, NV (PNS) – As they eye their inaugural football season this fall, the Gaveliers have question marks...
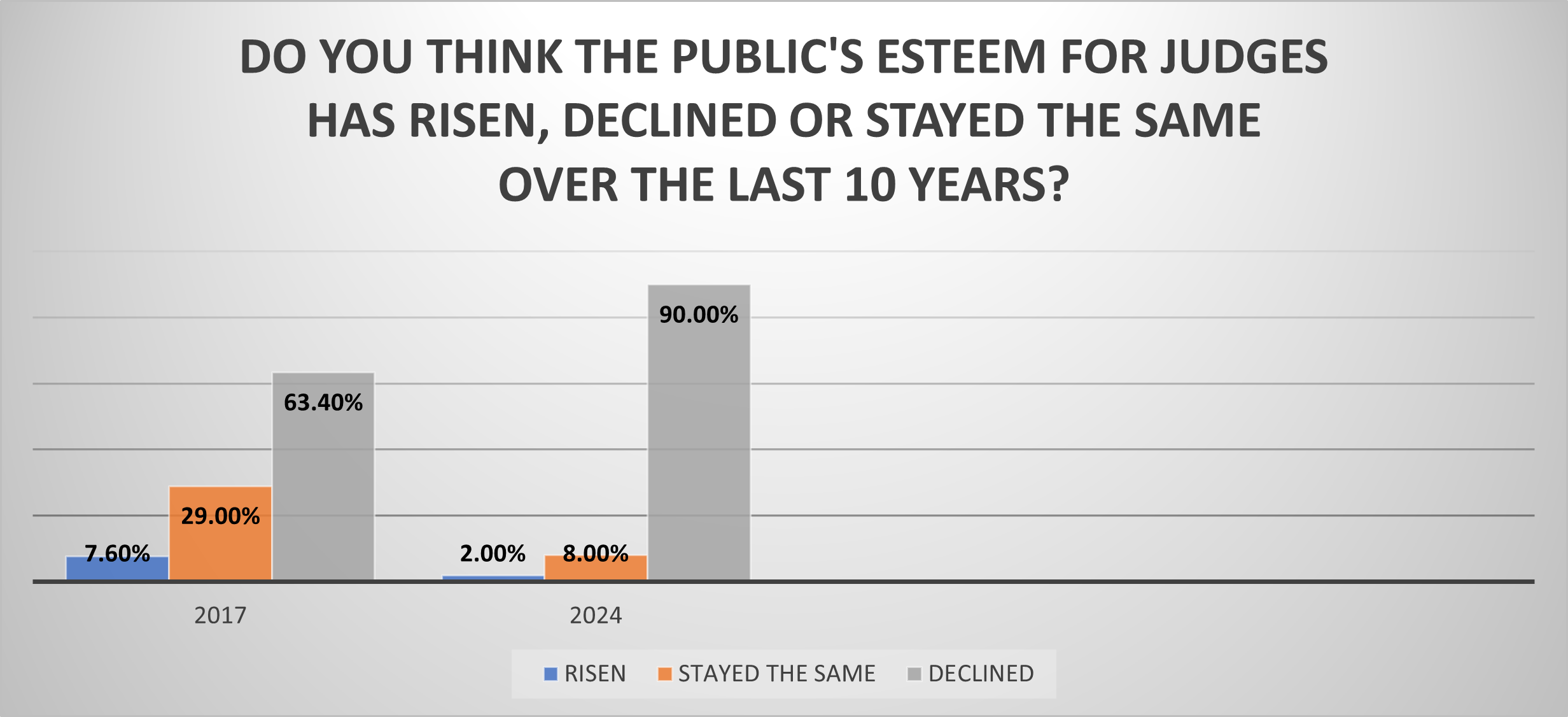
RENO, Nev. (March 8, 2024) — In what may reflect a devastating blow to the morale of the judiciary, 9 out...

In what may reflect a devastating blow to the morale of the judiciary, 9 out of 10 judges believe the publi...

RENO, Nev. (Jan. 26, 2024) — The nation’s oldest, largest and most widely attended school for judges �...